Table of Contents
In this blog, we will guide you through the process of enabling HSTS for Nextcloud on Apache, Nginx, and OpenLiteSpeed servers , a popular open-source suite for file synchronization and sharing.
This guide will also remove the warning you see below.
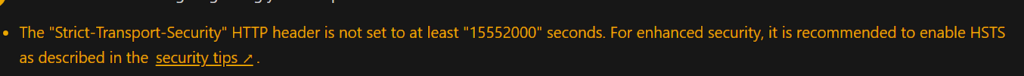
Enabling HTTP Strict Transport Security (HSTS) is an essential security measure for modern websites and web applications. It ensures that browsers communicate only over HTTPS, helping to protect users against common attacks like downgrade attacks, cookie hijacking, and more.
Enabling HSTS for Nextcloud on Apache
Locate and Update Apache Configuration File
Locate your Apache configuration file. Common locations include /etc/apache2/apache2.conf or /etc/httpd/httpd.conf. Open it with a text editor:
sudo nano /path/to/your/apache2.confSingle Domain Setup
Find the VirtualHost Section
Locate the <VirtualHost> section corresponding to your site.
Add HSTS Configuration
Inside the <VirtualHost> section, insert the following line:
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"Multi-Domain Setup
Find the VirtualHost Section for Each Domain
For each domain, locate its corresponding <VirtualHost> section in the configuration file.
Add HSTS Configuration to Each VirtualHost
Inside each <VirtualHost> section for each domain, insert the HSTS configuration line:
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"Restart Apache
After editing and saving the configuration file, restart the Apache server:
sudo systemctl restart apache2Notes:
- If you have a single domain with multiple subdomains, you can use the
includeSubDomainsdirective to apply the HSTS policy to all subdomains of that main domain. - If you are using wildcards in your VirtualHost configuration to match multiple subdomains, be cautious with the
includeSubDomainsdirective. Ensure that you understand the scope of the directive before using it in such a setup. - Test the changes in a staging or development environment first to ensure that they are working as expected.
Enabling HSTS for Nextcloud on Nginx
Locate and Update Nginx Configuration File
The Nginx configuration file can often be found in the /etc/nginx/sites-available/ directory. Open the configuration file for your domain:
sudo nano /etc/nginx/sites-available/your-domainSingle Domain Setup
Find the Server Block
Within the configuration file, locate the server block that corresponds to your site.
Add HSTS Configuration
Inside the server block, add the following line:
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload";Multi-Domain Setup
If you are hosting multiple domains on a single Nginx server, you’ll need to repeat the steps for each domain’s corresponding configuration file or server block.
Find the Server Block for Each Domain
For each domain, locate its corresponding server block in the configuration file.
Add HSTS Configuration to Each Server Block
Inside each server block for each domain, insert the HSTS configuration line:
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload";Restart Nginx
After editing and saving the configuration file(s), restart the Nginx server:
sudo systemctl restart nginxNotes:
- If you have a single domain with multiple subdomains, you can use the
includeSubDomainsdirective to apply the HSTS policy to all subdomains of that main domain. - If your Nginx setup uses a wildcard server block to handle multiple subdomains, be cautious with the
includeSubDomainsdirective. Understand the scope of the directive before using it in such a setup. - Make sure that HTTPS is already configured for the domain(s) before enabling HSTS.
- Test the changes in a staging or development environment first to ensure that they are working as expected.
- Remember to replace
your-domainwith the actual path to your domain’s configuration file.
Certainly! Here’s the revised text:
Enabling HSTS for Nextcloud on OpenLiteSpeed
OpenLiteSpeed is an open-source, high-performance web server. Here’s how you can enable HSTS on OpenLiteSpeed for different scenarios:
Access OpenLiteSpeed Web Admin Console
Log in to the OpenLiteSpeed web admin console. The URL is typically https://your-server-ip:7080.
In the navigation menu, go to Configuration > Listeners. Select the appropriate listener, typically the HTTPS listener.
Single Domain Setup
Add HSTS Configuration
Go to the Context tab, and then to the Header Operations section. Add the following line:
header add Strict-Transport-Security "max-age=63072000; includeSubDomains"Multi-Domain Setup
Select Each Domain’s Listener
For each domain, go to the Context tab for the corresponding listener.
Add HSTS Configuration for Each Domain
Inside each Context tab for each domain, insert the HSTS configuration line:
header add Strict-Transport-Security "max-age=63072000; includeSubDomains"Restart OpenLiteSpeed
After updating the configuration for each domain (if applicable), restart OpenLiteSpeed to apply the changes:
sudo systemctl restart openlitespeedNotes:
- If you have a single domain with multiple subdomains, the
includeSubDomainsdirective will apply the HSTS policy to all subdomains of that main domain. - Ensure that SSL/TLS is properly configured for the domain(s) before enabling HSTS.
- Carefully test the changes in a staging or development environment to confirm that they work as expected before applying them to a live server.
- The OpenLiteSpeed web admin console may require specific permissions or authentication, so ensure you have the necessary access rights.
OpenLiteSpeed Configuration via CLI
Locate OpenLiteSpeed Configuration Files
OpenLiteSpeed stores its main configuration file usually at /usr/local/lsws/conf/httpd_config.conf. Virtual host-specific configurations are often located in separate files within a directory like /usr/local/lsws/conf/vhosts/.
Open Main Configuration File
You can start by opening the main configuration file with a command like:
sudo nano /usr/local/lsws/conf/httpd_config.confLocate the Virtual Hosts Include Directive
Inside the main configuration file, look for an include directive that points to the virtual hosts’ configuration files. It might look like:
include /usr/local/lsws/conf/vhosts/*.confThis line tells OpenLiteSpeed to include all the .conf files in the specified directory as part of the configuration.
Based on the path specified in the include directive, navigate to the virtual hosts directory:
cd /usr/local/lsws/conf/vhosts/Here, you will find individual .conf files for each virtual host (domain) on your server.
Edit the Appropriate Virtual Host Configuration File
Identify the .conf file corresponding to the domain you want to configure, and open it with a text editor:
sudo nano /usr/local/lsws/conf/vhosts/your-domain.confAdd HSTS Configuration
Within the virtual host configuration file, locate the context or directive where you want to add the HSTS header, and insert the line:
header add Strict-Transport-Security "max-age=63072000; includeSubDomains"Restart OpenLiteSpeed
Finally, restart OpenLiteSpeed to apply the changes:
sudo systemctl restart openlitespeedNotes:
- Paths and filenames might vary based on your specific setup or any customizations.
- Always make a backup of any configuration file before making changes.
- Carefully test your changes in a development environment before applying them to a live server.
Conclusion
Enabling HSTS for nextcloud is an essential step in securing your installation. It requires only a few simple configurations in Apache, Nginx, or OpenLiteSpeed, and it goes a long way in protecting your users’ data.
If you have any questions or need further assistance, feel free to leave a comment below, and I’ll be glad to assist you. By prioritizing security with these steps, you can ensure a safer and more trustworthy experience for your Nextcloud users. Happy configuring!
