Table of Contents
The Aurora Malware, a sophisticated data stealer with reliable infrastructure and few detections, is being adopted by cybercrime syndicates. Researchers at SEKOIA have seen a rise in the quantity of Aurora samples and the number of C2 servers used to process them.
Caphaw/Redline, Raccoon and Aurora Malware Stealers on the Rise
The researchers claim that numerous advertisements for Redline, Raccoon, and Aurora stealing tools have been discovered on underground message boards with the express purpose of recruiting traffers and rating these tools. Multiple infection chains were recorded in October and November, resulting to Aurora stealer execution in the wild. Seven traffers teams have been detected actively distributing the stealer, including RavenLogs, BrazzersLogs, DevilsTraff, YungRussia, Gfbg6, SAKURA, and HellRide.
Aurora stealer is transmitted using phishing pages that seem like legitimate software download pages, such as remote access tools and bitcoin wallets. Other infection vectors include YouTube movies with links to phoney software and cheat catalogues, as well as SEO-enhanced fake software crack download websites.
Mostly what your 12 year-old CS:GO player will click.
Command and Control server communications
Upon execution, Aurora, a Golang-based information stealer, executes a number of commands through WMIC to gather fundamental host information, capture a screenshot of the victim’s desktop, and exfiltrate data to the C2 server.
The malware uses TCP connections to communicate, with port 8081 being the most often used one. The information that was stolen is in JSON format.
All messages abide by the same structure, each keys are described below:
- Browser: name of the browser where data was collected (ex: Mozilla, Chromium, etc.);
- Cache: content of the stolen file encoded in base64;
- FileName: name of the stolen file (e.g. cookies.sqlite, Login Data);
- GRB: likely the grabber configuration. Of note, SEKOIA.IO only observed the value “null”;
- Info: host fingerprint information, including:
- Name: a random name defined by threat actor;
- BuildID: name of the build, the value often matches a threat actor’s Telegram account;
- OS: Windows version;
- HWID: hardware ID;
- GPU: graphical card information;
- CPU: CPU name and vendor;
- RAM: amount of memory;
- Location: execution path of Aurora sample;
- Screen: size of the screen of the infected host;
- IP: expecting the IP address of the infected host but the value is always an empty string.
- MasterKey: encryption key used to read the data of the stolen file, for instance some browsers store the saved password encrypted;
- Path: always empty string;
- Type: type of the exfiltrated data (Browser-Mozilla, Screenshot, etc.).
Here’s an example of fingerprint information that was sent to the C2 Aurora Server:
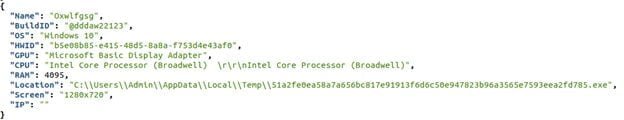
- It targets information stored in various web browsers (cookies, passwords, history, credit card information), cryptocurrency browser extensions that manage cryptocurrency wallets, such as Electrum, Ethereum, Exodus, Zcash, Armory, Bytecoin, Guarda, and Jaxx Liberty, and Telegram.
- It encapsulates all the stolen information from the infected host in a single base64-encoded JSON file and delivers it to the C2 through TCP ports 8081 or 9865.
- The malware author offers file grabber and loader functionality. It then executes the subsequent stage using a PowerShell command after downloading a fresh remote payload to the filesystem.
The Development of the Aurora Malware
The malware first appeared in April as a multi-function botnet capable of theft, downloading, and gaining remote access.
Even though its creators had ceased posting about it in June, a threat actor known as Cheshire began offering it for sale as Malware-as-a-Service (MaaS) in July. This was done to generate revenue. The MaaS operation was shut down at some point in late August, and from about that time, Telegram and other underground forums began marketing The malware as a thief rather than a botnet. In September, KO7MO started spreading word about the heist on an online community known as XSS. You may rent it for $250 per month, or you can buy a permanent license for $1,500 once and use it forever.
Find out more on the full blog post
