Cybersecurity researchers have found new cases of RapperBot malware used to build a botnet that can attack gaming servers with DDoS attacks.
Researchers from Fortinet FortiGuard Labs, Joie Salvio and Roy Tay, said in a paper that came out on Tuesday that this campaign is less like RapperBot than an older one that started in February and disappeared in mid-April for no clear reason.
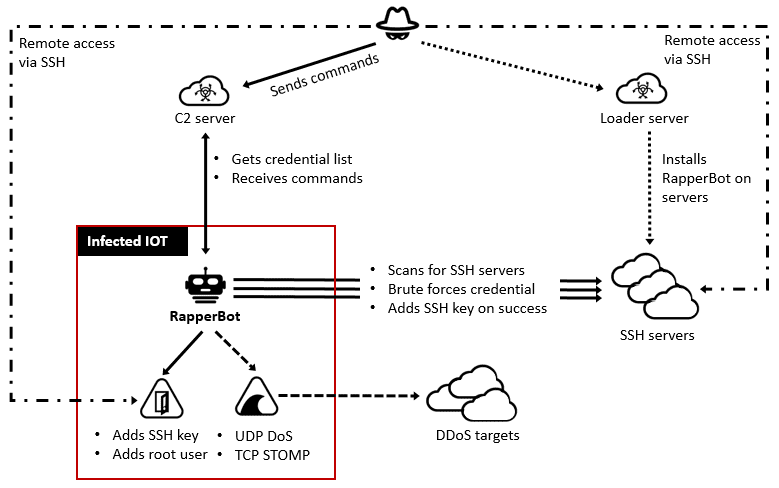
The network security company found out about RapperBot in August 2022. It is heavily based on the Mirai botnet, whose source code was leaked in October 2016, which led to many different versions.
What can it do?
The new version of the RapperBot malware can do brute-force Telnet attacks, as well as DoS attacks using the Generic Routing Encapsulation (GRE) tunneling protocol and UDP floods that target game servers running Grand Theft Auto: San Andreas.
The researchers said, “The Telnet brute-force code is mostly made for self-propagation and looks like the old Mirai Satori botnet.”
This was clear in the artifacts that were found after July 2022.
Attack Outcomes
When an attack is successful, the credentials used are sent back to the C2 server and the RapperBot payload is installed on the device that was broken into.
Attack Scope
Fortinet said that the RapperBot malware is made to only attack appliances that run on the ARM, MIPS, PowerPC, SH4, and SPARC architectures. If an appliance runs on an Intel chipset, the virus will stop spreading itself.
Also, it has been found that the October 2022 campaign has overlaps with other operations that used the malware as far back as May 2021. The Telnet spreader module first showed up in August 2021, but was taken out of later samples and put back in last month.
“Based on the undeniable similarities between this new campaign and the previously reported RapperBot campaign, it is highly likely that they are both being run by a single threat actor or by different threat actors who have access to a privately shared base source code,” the researchers said.
Read the full research article on fortinet

