Over the past week, hackers have launched a new campaign that has already infiltrated over 15,000 WordPress sites in an effort to trick users into visiting malicious question and answer websites.
A “smart black hat SEO tactic,” according to Sucuri researcher Ben Martin, “these malicious redirects appear to be aimed to improve the authority of the attacker’s sites for search engines.”
The strategy of search engine poisoning is intended to promote a “handful of phony low-quality Q&A sites” that share similar website-building templates and are administered by the same threat actor.
In contrast to past attacks of this type, in which just a small number of files are modified to lower footprint and evade detection, it is significant that the hackers are capable of modifying an average of over 100 files per website.
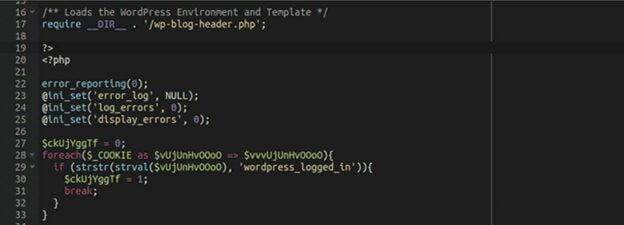
Commonly infected sites include wp-signup.php, wp-cron.php, wp-links-opml.php, wp-settings.php, wp-comments-post.php, wp-mail.php, xmlrpc.php, wp-activate.php, wp-trackback.php, and wp-blog-header.php.
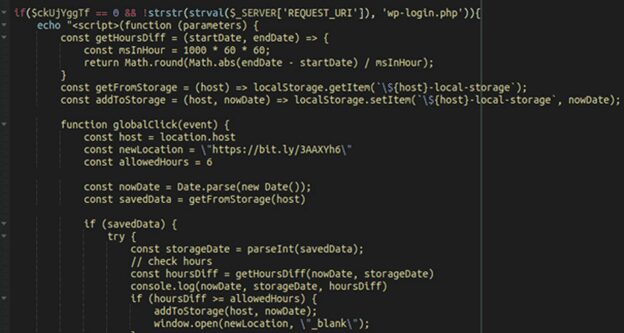
This broad infiltration enables malware to conduct redirects to destinations selected by the attacker. To minimize suspicion, it is important to note that redirects do not occur if the wordpress logged in cookie is present or if the current page is wp-login.php (the login page).
The campaign’s ultimate objective is to “attract more traffic to their bogus sites” and “raise the sites’ authority using false search result clicks so that Google ranks them higher and they receive more real organic search traffic.”
The injected code accomplishes this by initiating a redirect to a PNG image housed on a domain named “ois[.]is” that, rather than loading the picture, redirects the website visitor to the Google search result URL of a spam Q&A domain.
It is not immediately clear how the WordPress sites are compromised, and Sucuri stated that it did not observe any obvious plugin vulnerabilities being used in the campaign.
Nevertheless, brute-force attacks on WordPress administrator accounts are feared, making it imperative that user’s setup two-factor authentication and keep all software up-to-date
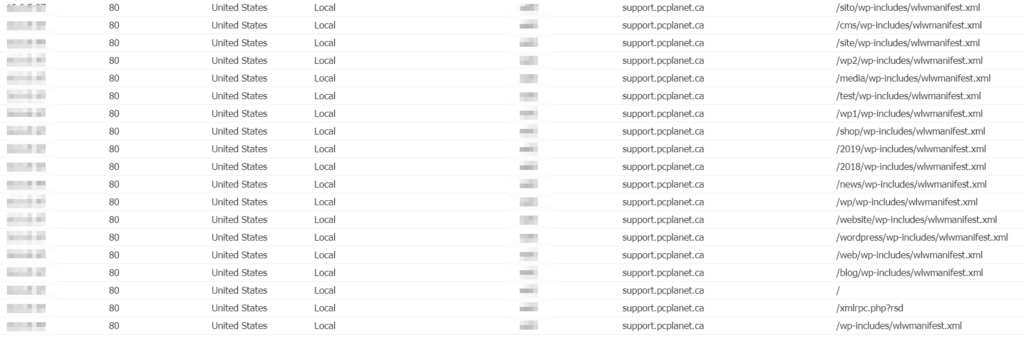
I can also say that I’ve been seeing quite a number of requests to the pages mentioned above


1 comment
Awesome post.