Nextcloud offers a powerful platform for data synchronization and collaboration. However, to secure Nextcloud is paramount to ensure the integrity and safety of your data. In this guide, we’ll explore various strategies and tools to help you secure your Nextcloud installation.
Implementing Geoblocking to Secure Nextcloud
Geoblocking restricts access to Nextcloud based on geographic location, adding a sophisticated layer of protection to your Nextcloud instance. By limiting unauthorized access from specific regions, geoblocking enhances security in several key ways. Here’s how you can set up geoblocking at both the Nextcloud and OS levels, along with an explanation of why it’s an essential security measure:
- Preventing Access from High-Risk Locations: Certain regions may be known for higher levels of cybercriminal activity. By blocking access from these locations, you minimize the risk of attacks originating from those areas.
- Compliance with Legal and Regulatory Requirements: Some jurisdictions have specific data protection laws that require businesses to restrict access to data based on geographic locations. Geoblocking helps in adhering to these legal obligations.
- Protection Against Brute-Force Attacks: By limiting access to specific regions where your organization operates or where legitimate users reside, you reduce the surface area for potential brute-force attacks.
- Reducing Bandwidth and Resource Abuse: Unwanted traffic from regions that are not relevant to your Nextcloud instance can consume valuable bandwidth and resources. Geoblocking can minimize unnecessary consumption and improve the performance for legitimate users.
- Customized User Experience: Geoblocking allows for a more tailored user experience by directing users from specific regions to localized versions of Nextcloud or providing content specific to their location.
- Enhanced Monitoring and Analytics: Tracking access attempts from different regions can provide insights into potential threats and allow for proactive security measures. Geoblocking logs can be analyzed to detect patterns indicative of malicious activity.
- Integration with Other Security Measures: Geoblocking can be part of a multi-layered security strategy, working in conjunction with firewalls, two-factor authentication, and other security protocols to create a robust defense against unauthorized access.
By implementing geoblocking, you not only secure Nextcloud but also demonstrate a commitment to safeguarding user data and adhering to best practices in cybersecurity. Whether you choose to apply geoblocking at the Nextcloud level using the Geoblocker app or at the OS level using tools like GeoIP, the enhanced security measures will contribute to a more resilient and reliable Nextcloud environment.
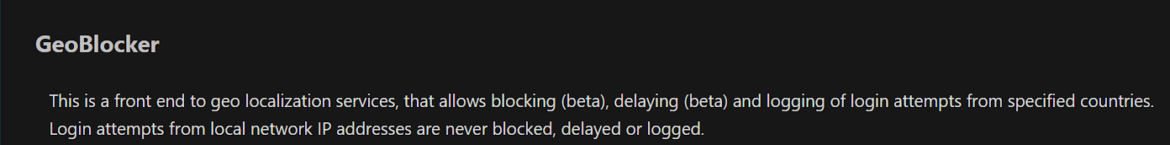
Using the Geoblocker App
The Geoblocker app in Nextcloud provides an easy way to restrict access based on geographic locations.
Install the Geoblocker App
- Navigate to the Apps menu in Nextcloud.
- Search for “Geoblocker” and click “Download and enable.”
- Go to Settings > Security to configure the Geoblocker.
Configure the Geoblocker App
- Select the geographical regions to allow or block.
- Choose the blocking method, such as blocking login or all access.
- Configure logging to keep track of blocked attempts.
- Save the settings.
OS-Level Geoblocking
Implementing geoblocking at the operating system level can provide additional protection. This can be achieved using tools like geoip with iptables.
Configure Firewall with GeoIP
Here’s a step-by-step guide for setting up geoblocking using GeoIP on a Linux system:
- Install the GeoIP module:
sudo apt-get install xtables-addons-common- Download the GeoIP database:
sudo /usr/lib/xtables-addons/xt_geoip_dl- Build the GeoIP database:
sudo /usr/lib/xtables-addons/xt_geoip_build /usr/share/xt_geoip- Add rules to block or allow specific countries: To block access from a specific country (e.g., Russia – RU):
sudo iptables -A INPUT -m geoip --src-cc RU -j DROPTo allow access only from specific countries (e.g., United States – US, Canada – CA):
sudo iptables -A INPUT -m geoip ! --src-cc US,CA -j DROP- Save the iptables rules to make them persistent across reboots:
sudo iptables-save > /etc/iptables/rules.v4Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) adds an indispensable layer of security to Nextcloud by requiring two separate forms of identification for user authentication. This multi-step verification process ensures that even if a password is compromised, an attacker would still need access to the second form of identification, such as a mobile device or a hardware token, to gain entry. Here’s why implementing 2FA is a crucial security measure for Nextcloud:
- Protection Against Password Breaches: In an age where password breaches are common, relying solely on passwords can leave your Nextcloud instance vulnerable. 2FA adds an additional barrier, making unauthorized access more challenging.
- Mitigation of Phishing Attacks: Even if a user’s credentials are stolen through phishing, the attacker would need physical access to the second authentication factor (e.g., a mobile phone), rendering the stolen credentials useless by themselves.
- Enhanced User Accountability: With 2FA, you can ensure that only authorized individuals have access to specific resources, enhancing the accountability of users within your organization.
Enable 2FA in Nextcloud
Here’s how to set up 2FA in Nextcloud, focusing on TOTP (Time-based One-Time Password) but also mentioning other supported 2FA methods.
Navigate to Security Settings
- Log in as an administrator to your Nextcloud instance.
- Go to Settings > Security.
Enable TOTP
- Find the “Two-Factor TOTP Provider” section.
- Click “Enable.”
TOTP works with various authenticator apps, such as Google Authenticator or Authy, on smartphones.
Other Supported 2FA Methods
Nextcloud also supports other 2FA methods like U2F (Universal 2nd Factor) and SMS. These can be enabled similarly to TOTP and require corresponding hardware or services.
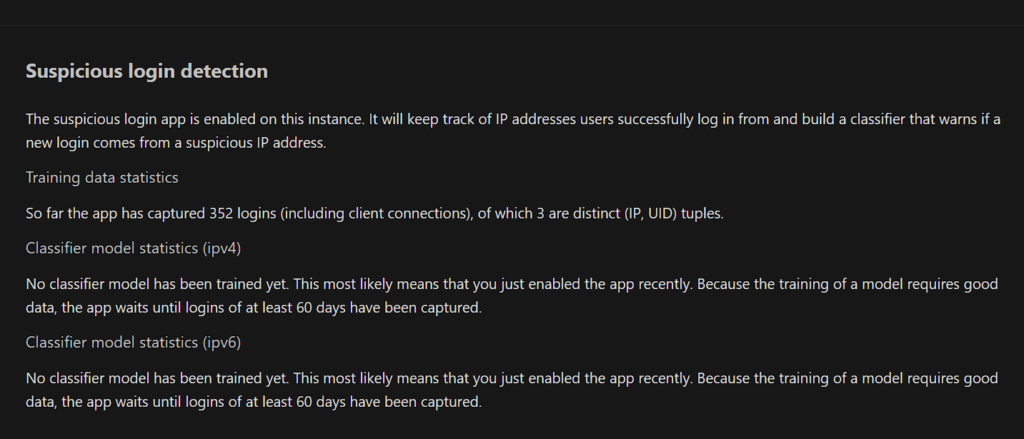
Suspicious Login Detection
This feature uses machine learning to detect and warn about suspicious login attempts.
Setting Up Suspicious Login Detection
- Install the Suspicious Login app from the Nextcloud app store.
- Configure the app to set up notification methods and sensitivity.
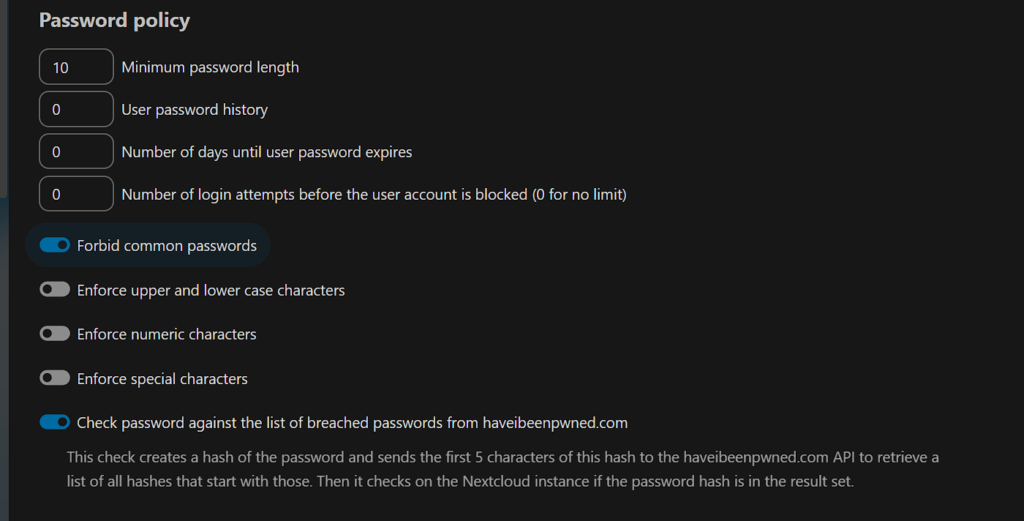
Implementing Strong Password Policies
Password policies enforce strong passwords, reducing the risk of brute-force attacks.
Read about managing users and passwords on Ubuntu
Configure Password Policies in Nextcloud
- Go to Security settings in Nextcloud admin.
- Set password length, complexity, and expiration rules.
OS-Level Password Policies
- Configure PAM (Pluggable Authentication Module) to enforce strong passwords at the system level.
OS-Level Security Measures to Secure Nextcloud
Securing Nextcloud is not just about configuring the application itself; the underlying operating system must also be fortified. Here are some essential OS-level security practices.
Discover more about basic Linux commands
Regular Updates
Keeping the OS and all installed software up to date is vital to ensure that known vulnerabilities are patched.
Steps to Automate Updates on Ubuntu
- Install the unattended-upgrades package:
sudo apt-get install unattended-upgrades- Configure unattended-upgrades by editing
/etc/apt/apt.conf.d/50unattended-upgrades. - Enable automatic updates:
sudo dpkg-reconfigure --priority=low unattended-upgrades- Verify that updates are working by checking the log files in
/var/log/unattended-upgrades.
Firewall Configuration
A well-configured firewall is a primary defense against unauthorized access.
Using UFW on Ubuntu
- Install UFW (Uncomplicated Firewall):
sudo apt-get install ufw- Allow necessary ports (e.g., 80 for HTTP, 443 for HTTPS):
sudo ufw allow 80,443/tcp- Enable UFW:
sudo ufw enable- Verify the rules:
sudo ufw statusSecure SSH Access to Secure Nextcloud
Securing SSH (Secure Shell) access is a crucial step in minimizing the risk of unauthorized remote access to the server where Nextcloud is hosted. Here’s a comprehensive guide to enhancing SSH security.
Use SSH Keys
Using SSH keys instead of passwords adds an extra layer of security.
Generate an SSH Key Pair
- Open a terminal on your local machine.
- Generate an SSH key pair with the
ssh-keygencommand:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"This will create a 4096-bit RSA key pair.
- Secure the private key by setting a strong passphrase when prompted.
Add the Public Key to the Server
- Copy the public key to the server using the
ssh-copy-idcommand:
ssh-copy-id user@serverReplace user@server with your username and server’s IP address or hostname.
- Verify the key-based authentication by SSHing into the server:
ssh user@serverYou should be prompted for the passphrase of your private key, not the user’s password.
Disable Root Login and Change SSH Port
Disabling root login and changing the default SSH port adds additional security layers.
Edit the SSH Configuration File
- Open the SSH configuration file on the server:
sudo nano /etc/ssh/sshd_config- Disable root login by finding the line with
PermitRootLoginand setting it tono:
PermitRootLogin noIf the line doesn’t exist, add it.
- Change the SSH port by finding the line with
Portand setting it to a non-default value, like 2222:
Port 2222If the line doesn’t exist, add it.
- Save the file and exit the editor.
Restart SSH to Apply Changes
- Restart the SSH service to apply the changes:
sudo systemctl restart ssh- Verify the new configuration by SSHing into the server with the new port:
ssh -p 2222 user@serverHarden PHP Configuration to Secure Nextcloud
Nextcloud runs on PHP, so securing PHP is an essential part of hardening Nextcloud.
Find out how to install PHP on Ubuntu
Disable Unnecessary PHP Functions
- Edit the
php.inifile (location depends on the PHP version). - Find or add the
disable_functionsline:
disable_functions = exec,passthru,shell_exec,system- Restart the web server to apply the changes.
Set Appropriate Permissions
- Set the correct owner for Nextcloud files:
sudo chown -R www-data:www-data /var/www/nextcloud- Set secure file permissions:
sudo find /var/www/nextcloud -type f -exec chmod 0640 {} \;
sudo find /var/www/nextcloud -type d -exec chmod 0750 {} \;Protecting Nextcloud from Malware
Use Nextcloud’s Antivirus App to Secure Nextcloud
Nextcloud offers an antivirus app that integrates with ClamAV, a popular open-source antivirus engine. This combination allows for continuous scanning of uploaded files and periodic scans of existing data.
Install and Configure ClamAV
Install ClamAV and ClamAV Daemon
- Update the package lists:
sudo apt-get update- Install ClamAV and ClamAV Daemon:
sudo apt-get install clamav clamav-daemonUpdate ClamAV’s Signatures
- Update the virus database to ensure that ClamAV can detect the latest threats:
sudo freshclam- Enable automatic updates by editing
/etc/clamav/freshclam.confand setting:
Checks 24This will update the virus signatures 24 times a day.
Install the Antivirus App for Files in Nextcloud
- Log in to Nextcloud as an administrator.
- Go to the Apps menu.
- Search for “Antivirus for files” in the search bar.
- Click “Download and enable” to install the app.
Configure the Antivirus App to Use ClamAV
- Go to Settings > Security in Nextcloud.
- Find the “Antivirus Configuration” section.
- Select “Daemon (Socket)” as the mode to connect to ClamAV.
- Set the hostname and port (usually
localhostand3310). - Choose the desired action for infected files, such as “Only log” or “Delete file.”
- Save the settings.
Regularly Scan for Malware
- Open a terminal on the server.
- Run a recursive scan on Nextcloud’s data directory:
sudo clamscan -r /path/to/nextcloud/dataReplace /path/to/nextcloud/data with the actual path to Nextcloud’s data directory.
- Consider setting up a cron job to automate regular scans. For example, to run a scan every day at 3:00 AM:
0 3 * * * sudo clamscan -r /path/to/nextcloud/data >/dev/null 2>&1Edit the cron table with sudo crontab -e and add the above line.
Protecting the System from Malware
Use Intrusion Detection Systems (IDS) to Enhance Security
Intrusion Detection Systems (IDS) play a vital role in securing Nextcloud installations and Linux servers by monitoring and analyzing network traffic for suspicious activities. Implementing IDS solutions like Fail2Ban, Snort, and Suricata can provide robust protection against various threats, including brute-force attacks, malware, and unauthorized access attempts. Here’s an overview of these tools:
Fail2Ban
Fail2Ban is an intrusion prevention software that protects Linux servers from brute-force and dictionary attacks. It operates by:
- Monitoring Logs: Fail2Ban scans system logs for patterns indicating failed login attempts or suspicious behavior.
- Banning Offenders: Upon detecting repeated failures from an IP address, Fail2Ban temporarily bans the address, preventing further access.
- Customizable Rules: Administrators can configure custom rules, defining the number of failed attempts allowed and the duration of the ban.
- Integration with Firewalls: It works seamlessly with iptables and other firewall management tools, enabling swift response to threats.
Install Fail2Ban
- Update the package lists:
sudo apt-get update- Install Fail2Ban:
sudo apt-get install fail2banConfigure Fail2Ban for Nextcloud
- Create a custom filter for Nextcloud by creating a file
/etc/fail2ban/filter.d/nextcloud.confwith the following content:
[Definition]
failregex={"reqId":".*","remoteAddr":"<HOST>","app":"core","message":"Login failed: '.*' \(Remote IP: '<HOST>'\)"
ignoreregex =- Create a jail configuration for Nextcloud by editing
/etc/fail2ban/jail.localand adding:
[nextcloud]
enabled = true
filter = nextcloud
port = 80,443
logpath = /path/to/nextcloud/data/nextcloud.log
maxretry = 3
bantime = 3600Adjust the logpath to the actual path of your Nextcloud log file.
- Restart Fail2Ban to apply the changes:
sudo systemctl restart fail2banLearn about additional security with Fail2Ban or learn more about Fail2Ban
Snort
Snort is a well-known open-source network intrusion detection system (NIDS) that offers real-time traffic analysis and packet logging. Key features include:
- Signature-Based Detection: Snort uses predefined signatures to identify known threats in network traffic.
- Anomaly Detection: It can also detect unusual patterns or behavior that may signify an attack, even if the signature is unknown.
- Extensible: Snort’s community and commercial support provide a rich set of plugins, rules, and configurations to tailor its behavior.
- Scalable: Suitable for various environments, from small businesses to large enterprises, providing consistent protection.
Suricata
Suricata is another open-source network IDS, Intrusion Prevention System (IPS), and Network Security Monitoring engine. Its features are:
- Multi-Threading: Suricata is designed to utilize multi-core CPUs efficiently, offering high performance.
- Protocol Analysis: It provides deep inspection of many protocols, including HTTP, TLS, and DNS, allowing for detailed analysis.
- Flexible Rule System: Suricata’s powerful and adaptable rule system enables custom detection logic, adapting to specific threats and environments.
- Integration with Threat Intelligence: Suricata can integrate with various threat intelligence feeds, enhancing its ability to detect emerging threats.
Use Linux Malware Detect (LMD)
Linux Malware Detect (LMD) is a malware scanner specifically designed to detect and remove malware on Linux systems.
Download and Install LMD
- Download LMD:
wget http://www.rfxn.com/downloads/maldetect-current.tar.gz- Extract the archive:
tar -xvf maldetect-current.tar.gz- Navigate to the extracted directory:
cd maldetect-*- Install LMD:
sudo ./install.shConfigure LMD
- Edit the configuration file
/usr/local/maldetect/conf.maldet. - Set the email alerts, daily update checks, and other preferences as needed.
- Configure the scan options, such as scan depth and file types.
Run a Scan
- Run a manual scan on a specific directory:
sudo maldet -a /path/to/scanSet Up Daily Scans with Cron
- Edit the cron file for LMD:
sudo crontab -e- Add a daily scan job, for example:
0 2 * * * /usr/local/sbin/maldet -a /path/to/scan >/dev/null 2>&1This will run a scan every day at 2:00 AM.
Conclusion
Securing Nextcloud requires a multifaceted approach, encompassing both application-level and OS-level measures. By implementing geoblocking, 2FA, suspicious login detection, strong password policies, and robust OS-level security practices, administrators can build a secure and resilient Nextcloud environment.
For further details on any of these topics, always refer to Nextcloud’s official documentation and consult with security professionals as needed.